

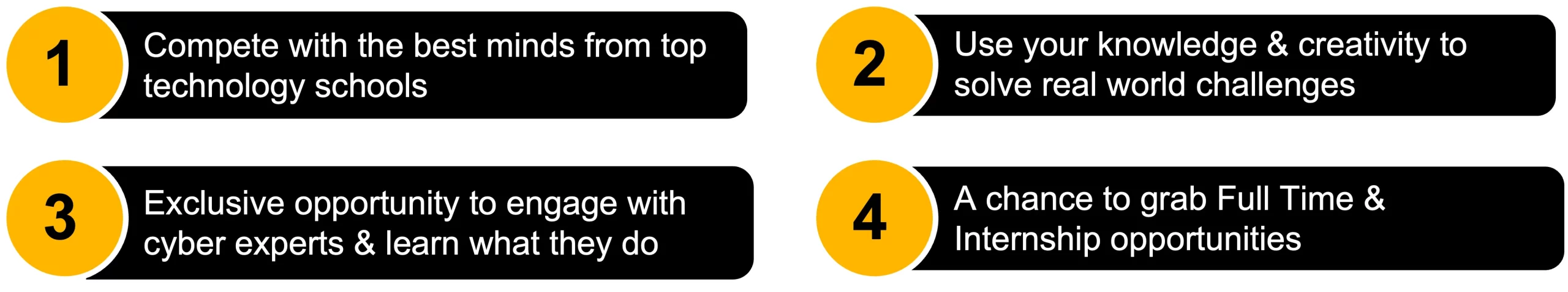
The real-world challenges pushed us to think quickly and creatively as we built and presented an application within a tight deadline. Meeting talented problem solvers from across the country and working well with my team made the experience exciting, intense, and fun.


Our team had an amazing time at PwC's 6-hour hackathon, solving a problem with new teammates. Seamless collaboration led us to the top 5, and we proudly became 1st runner-up. A big thanks to our mentor for their invaluable insights, making the experience both memorable and rewarding!


Thank you for organizing such an exciting event! A key highlight was networking with talented problem solvers from across the country. The real-world problem statements pushed us to think quickly and adapt to a strict tech stack, learning new technologies within just 6 hours. It was a thrilling, fun, and invaluable learning experience.



Elevate your code and prove your superior skills compared to your peers in all AI Protected skill Test.
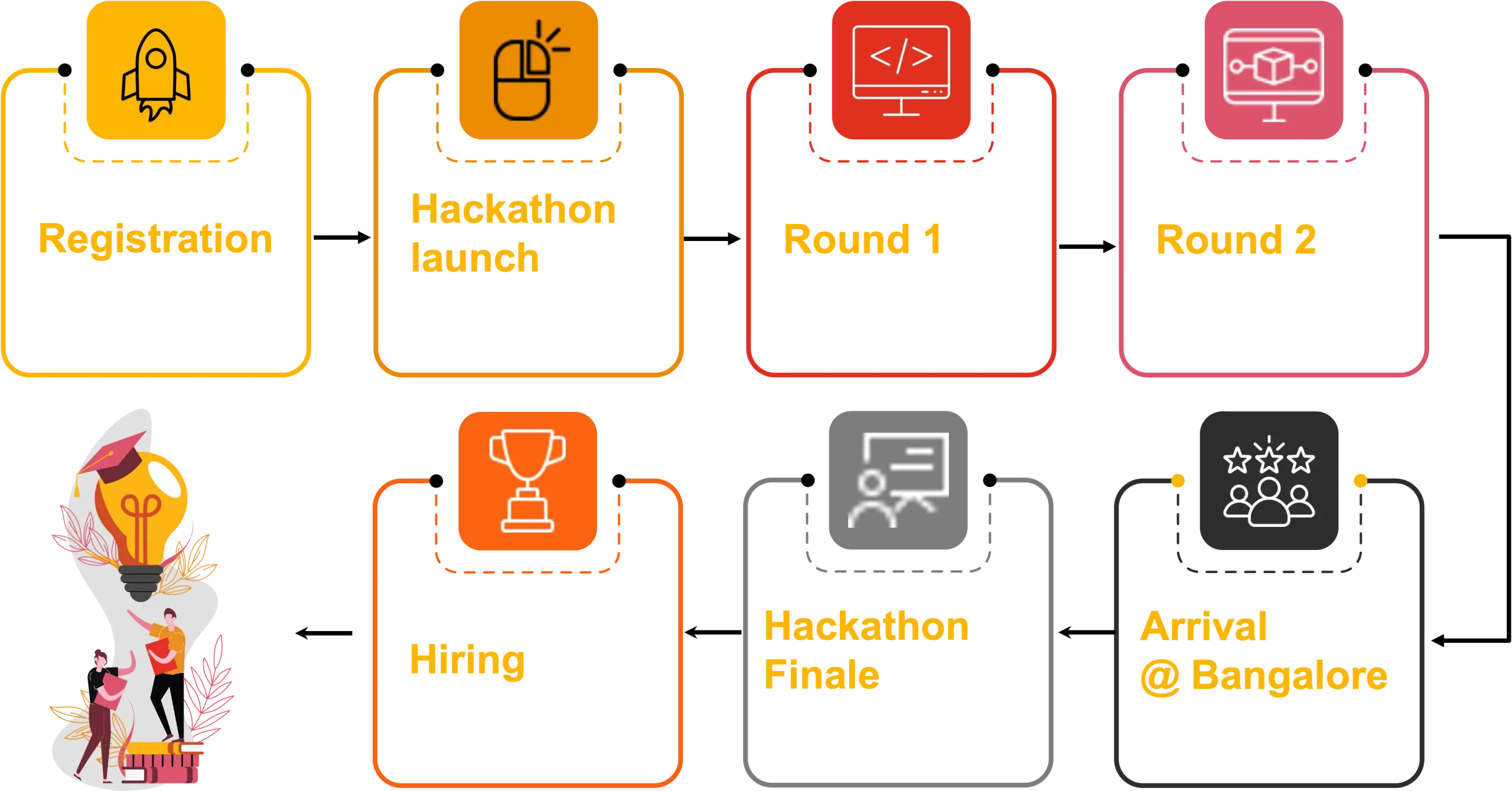
Candidates who are participating from the list of identified colleges will receive invitations for Round 1 of the hackathon. This initial round will entail an AI-proctored online assessment.



Hands-on exercise to solve a tech challenge, designed as a gamified application. The focus of this round would be to gauge the candidate’s understanding about common security vulnerabilities and ways to exploit those as an ethical hacker.



Bring your innovative ideas to life and showcase your app development expertise through captivating presentations.
Candidates will be invited for Round 3 (on campus) which will consist of a hands-on exercise to build an application, followed by a project presentation. This round aims to build secure applications using standard cyber security libraries, within a limited timeframe, while working in a team. The candidates will also be given time to present the application and explain the security measures implemented in their applications.










© 2024 PwC. All rights reserved. Not for further distribution without the permission of PwC. “PwC” refers to the network of member firms of PricewaterhouseCoopers International Limited (PwCIL), or, as the context requires, individual member firms of the PwC network. Each member firm is a separate legal entity and does not act as agent of PwCIL or any other member firm. PwCIL does not provide any services to clients. PwCIL is not responsible or liable for the acts or omissions of any of its member firms nor can it control the exercise of their professional judgment or bind them in any way. No member firm is responsible or liable for the acts or omissions of any other member firm nor can it control the exercise of another member firm’s professional judgment or bind another member firm or PwCIL in any way.
